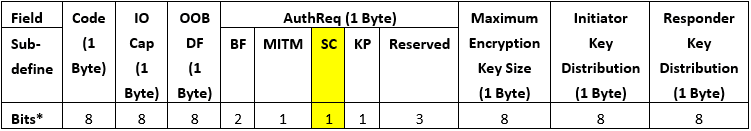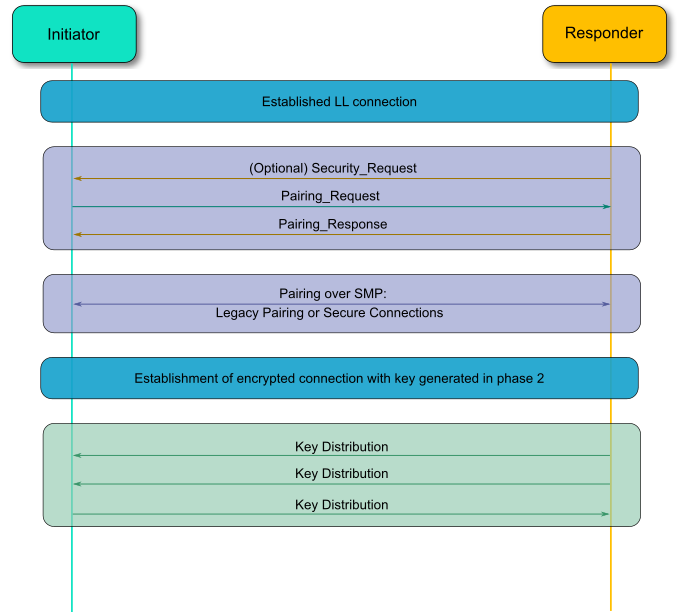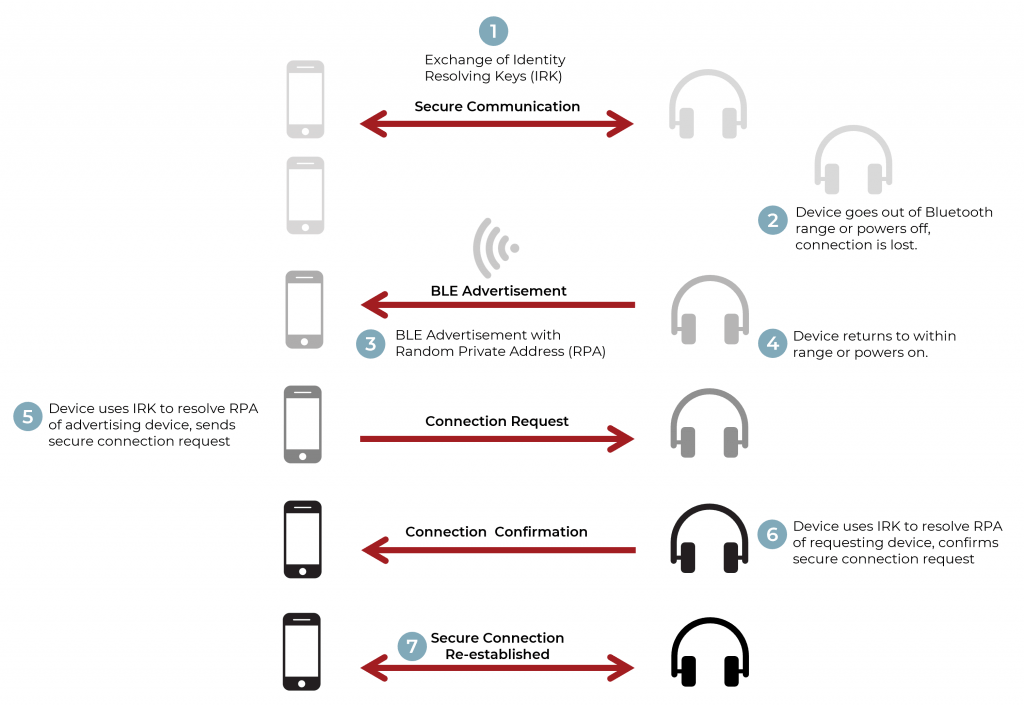
How to Implement Bluetooth Low Energy Security and Privacy in Wireless Devices - Contract Engineering, Product Design & Development Company - Cardinal Peak
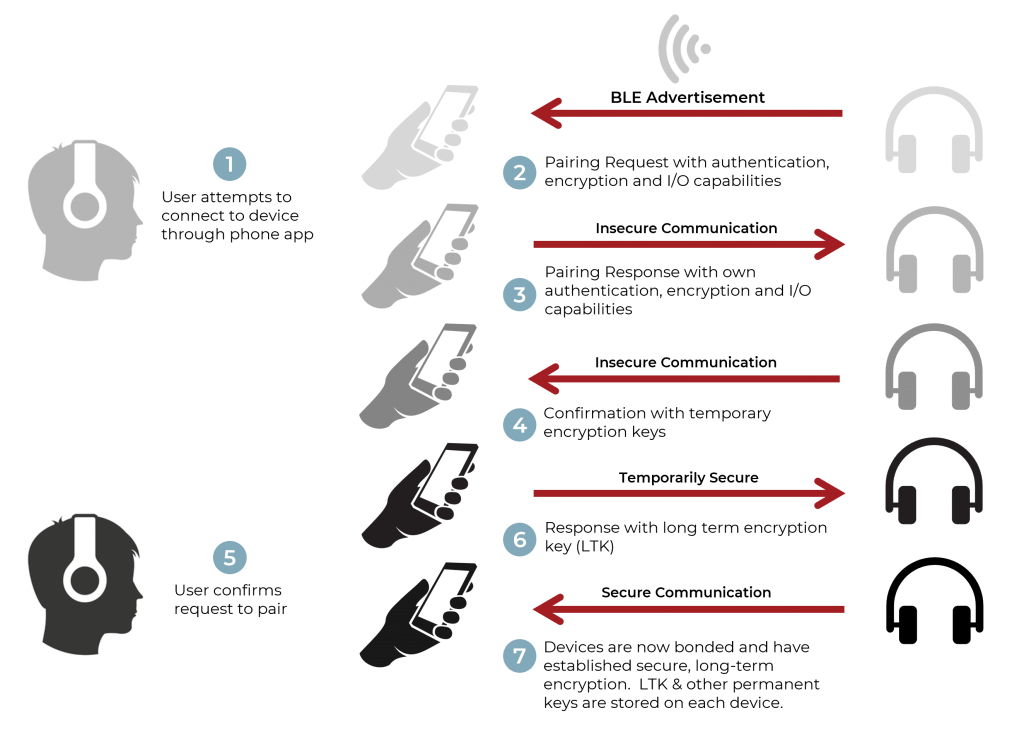
How to Implement Bluetooth Low Energy Security and Privacy in Wireless Devices - Contract Engineering, Product Design & Development Company - Cardinal Peak