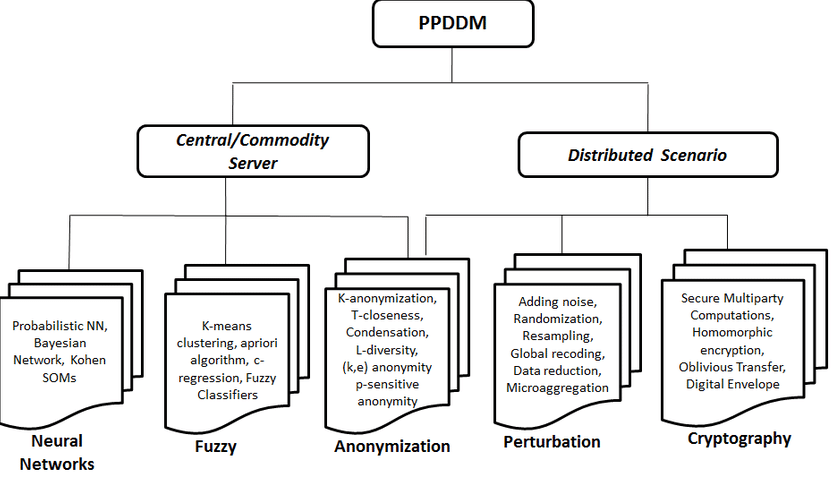
Classification of Privacy preserving techniques III. RELATED WORK This... | Download Scientific Diagram

Privacy Preserving Data Mining Techniques knowledge from large volumes... | Download Scientific Diagram

Applied Sciences | Free Full-Text | A Comprehensive Survey on Privacy-Preserving Techniques in Federated Recommendation Systems

New Era Of Data Monetization: Advances In Data-Sharing Technologies Made It Easy To Share Data While Preserving Security And Privacy | Snowdrop Solution






![PDF] A Brief Survey on Privacy Preserving Techniques in Data Mining | Semantic Scholar PDF] A Brief Survey on Privacy Preserving Techniques in Data Mining | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/48a742320cdf046020d7f7dfd9000714cce57223/4-Table1-1.png)

![PDF] Techniques of Data Perturbation for Privacy Preserving Data Mining | Semantic Scholar PDF] Techniques of Data Perturbation for Privacy Preserving Data Mining | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/060134f1210209c83bc24e18fc3582b7c4e7aa93/2-Figure1-1.png)