Does anyone have experience with bluetooth hacking (or hijacking?)? And enabling Kali vm BT : r/hacking

Mastering Kali Linux for Advanced Penetration Testing: Secure your network with Kali Linux 2019.1 – the ultimate white hat hackers' toolkit, 3rd Edition (English Edition) eBook : Velu, Vijay Kumar, Beggs, Robert:

Amazon.com: Panda Bluetooth 4.0 USB Nano Adapter - Windows XP/Vista/7/8/8.1/10/11, Mint, Ubuntu, Fedora, openSUSE, Lubuntu, Zorin, BackTrack5 R3, Kali Linux, Raspbrian Wheezy and OpenELEC : Electronics





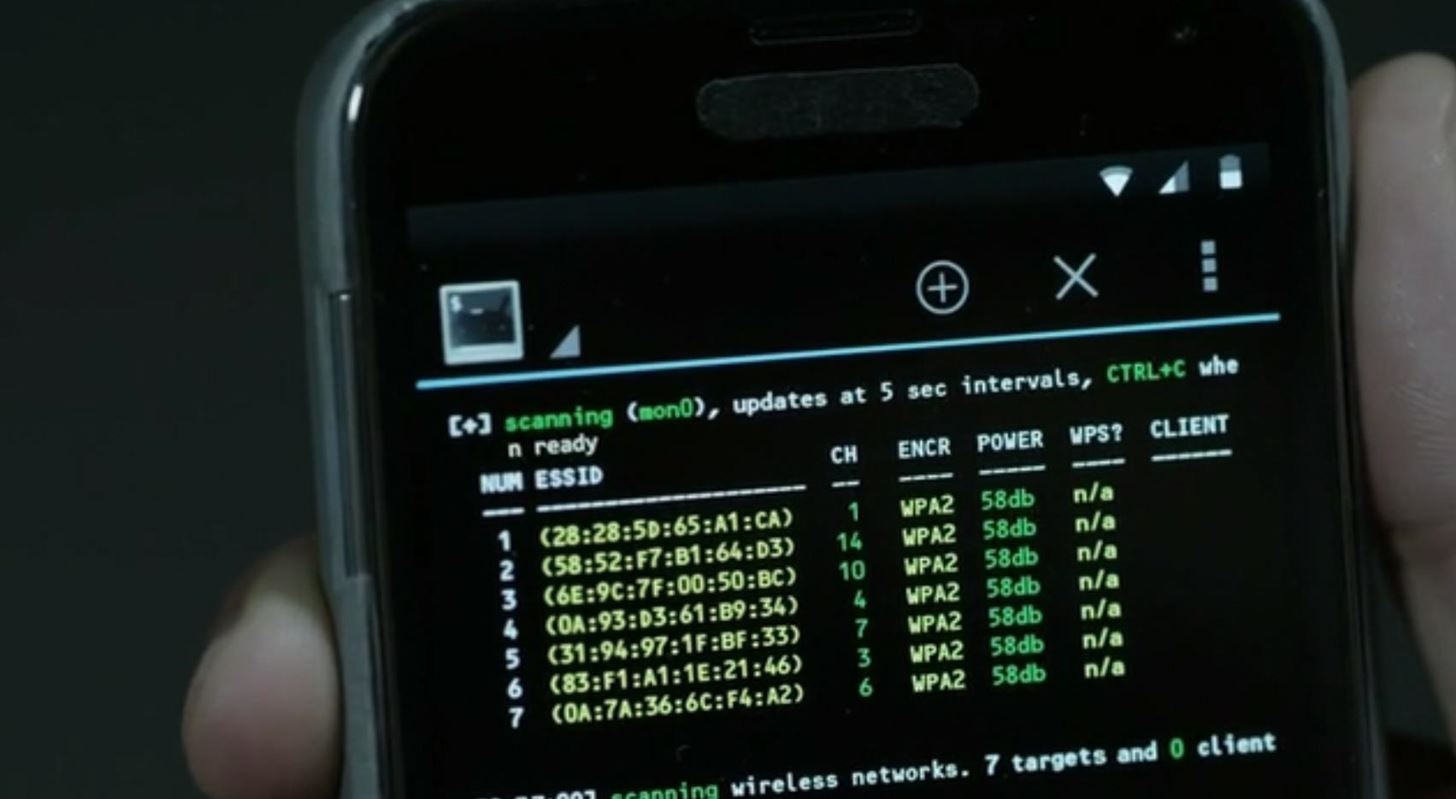
![Snoop on Bluetooth Devices Using Kali Linux [Tutorial] - YouTube Snoop on Bluetooth Devices Using Kali Linux [Tutorial] - YouTube](https://i.ytimg.com/vi/lXLrb1pfnrs/hq720.jpg?sqp=-oaymwE7CK4FEIIDSFryq4qpAy0IARUAAAAAGAElAADIQj0AgKJD8AEB-AHUBoAC4AOKAgwIABABGEkgUChlMA8=&rs=AOn4CLBJAJMdhoeyfTgGErK2XRHr1nmLbQ)
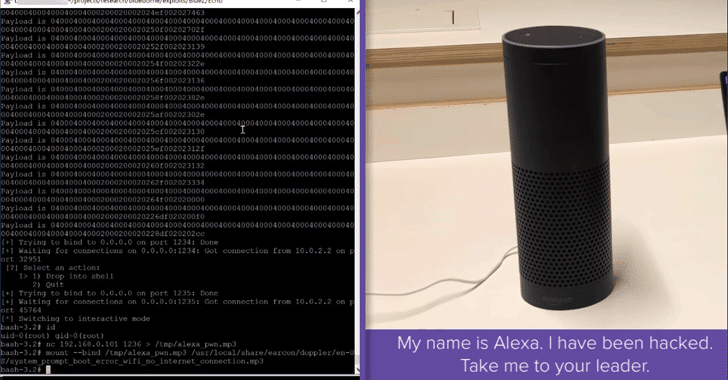


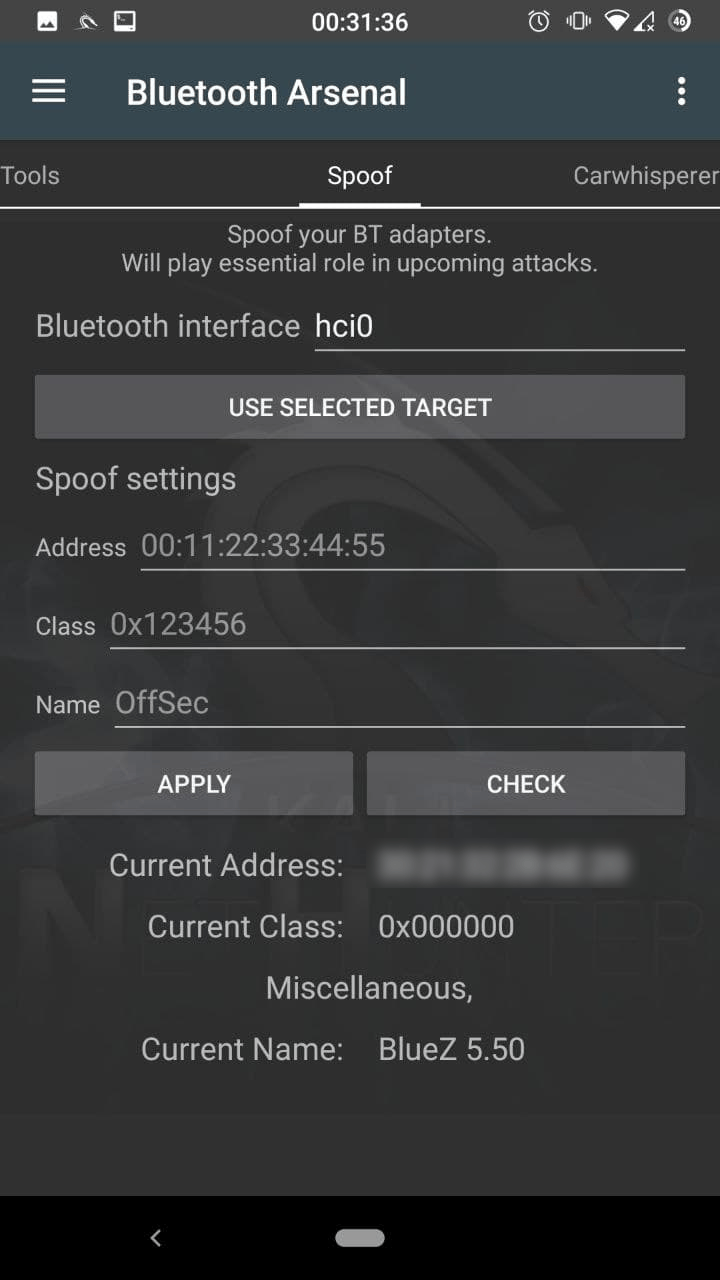
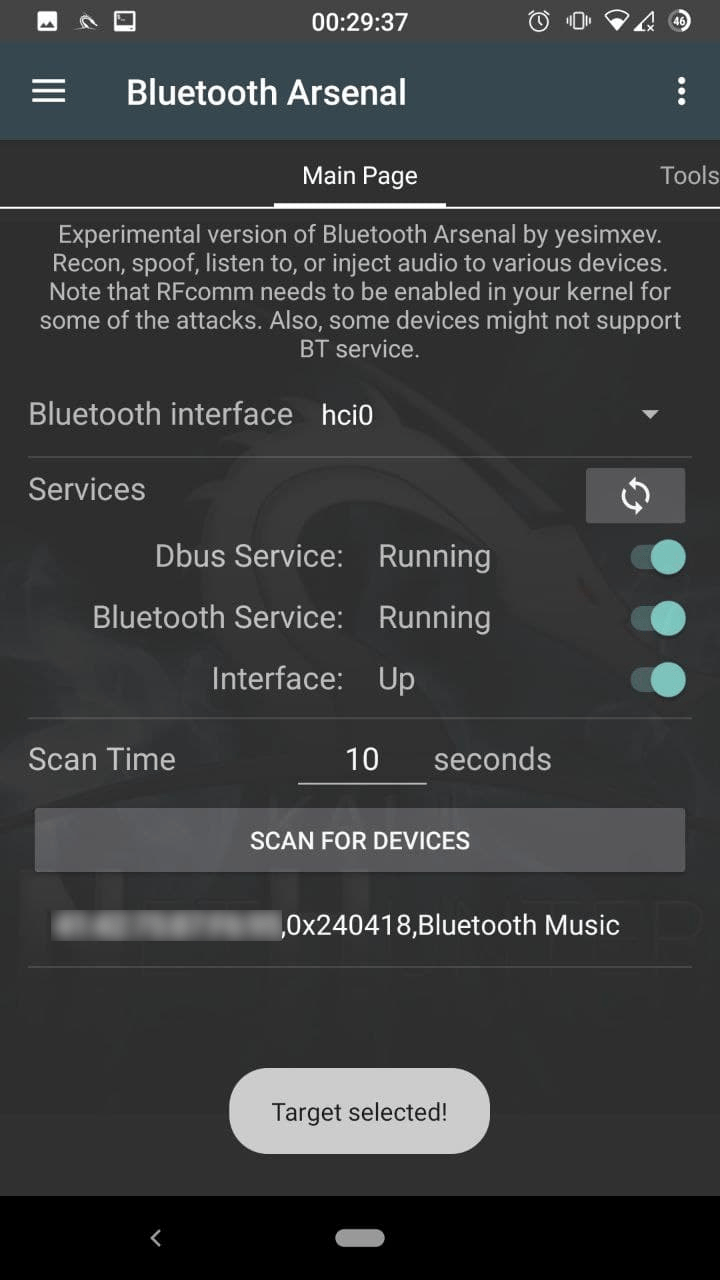




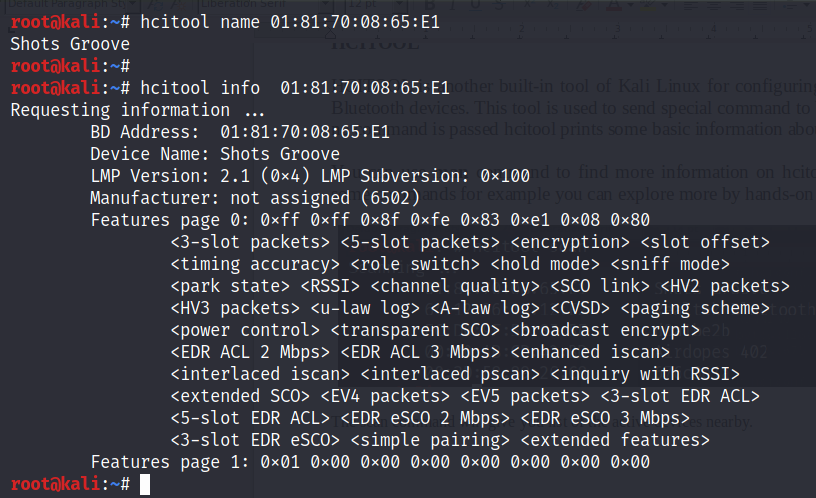


![Snoop on Bluetooth Devices Using Kali Linux [Tutorial] - YouTube Snoop on Bluetooth Devices Using Kali Linux [Tutorial] - YouTube](https://i.ytimg.com/vi/JmQk4Yp9bww/maxresdefault.jpg)