![Reusable Fuzzy Extractor Based On The Learning-with-error Assumption Secure Against Quantum Attacks Cho; Chongwon ; et al. [HRL Laboratories, LLC] Reusable Fuzzy Extractor Based On The Learning-with-error Assumption Secure Against Quantum Attacks Cho; Chongwon ; et al. [HRL Laboratories, LLC]](https://uspto.report/patent/app/20200145206/US20200145206A1-20200507-D00000.png)
Reusable Fuzzy Extractor Based On The Learning-with-error Assumption Secure Against Quantum Attacks Cho; Chongwon ; et al. [HRL Laboratories, LLC]
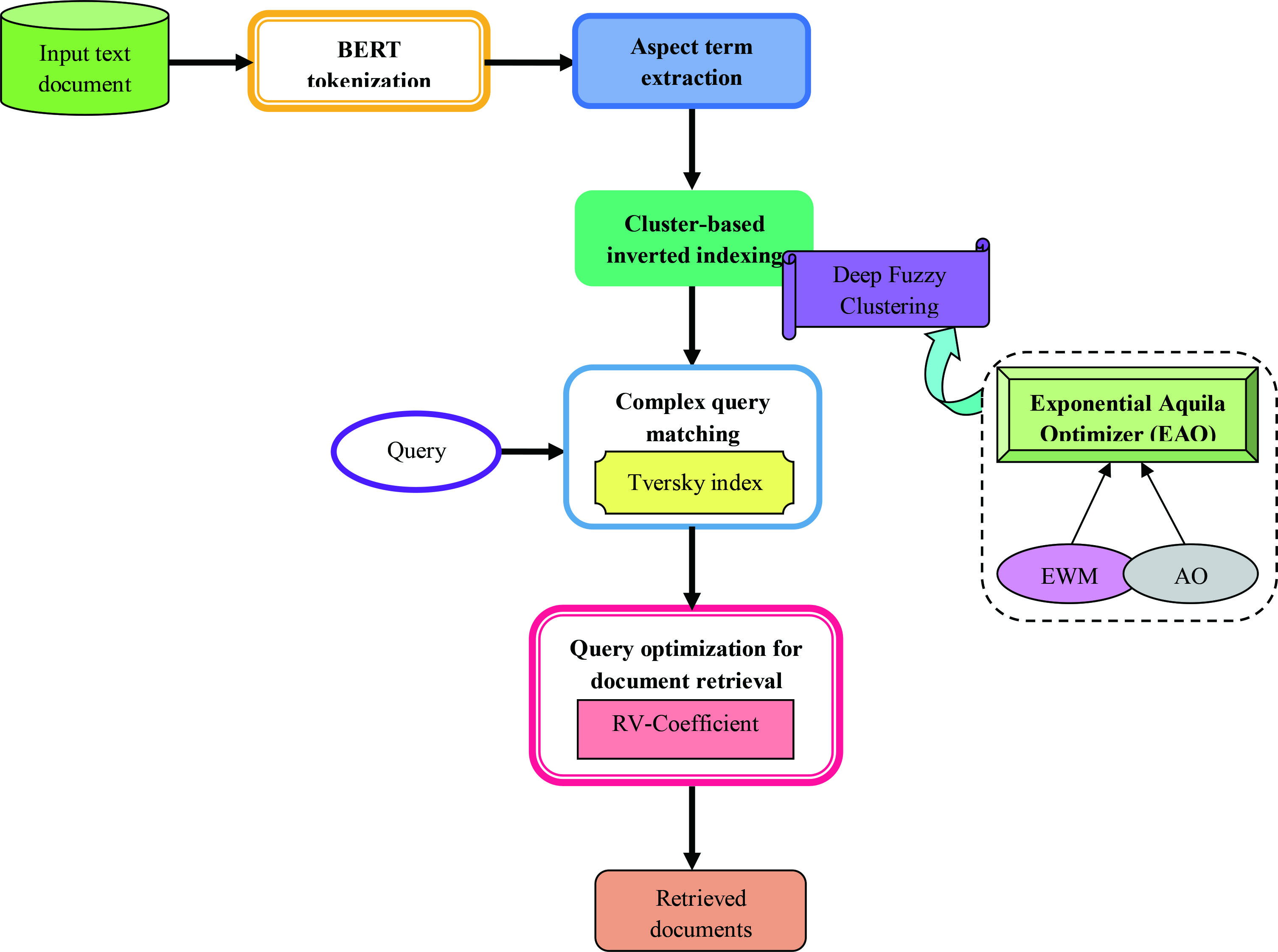
Aspect term extraction and optimized deep fuzzy clustering-based inverted indexing for document retrieval - IOS Press
![PDF] Fuzzy Extractors: How to Generate Strong Keys from Biometrics and Other Noisy Data | Semantic Scholar PDF] Fuzzy Extractors: How to Generate Strong Keys from Biometrics and Other Noisy Data | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/5f00233479dd7d08475f708c911c5b3999a78d8f/4-Figure1-1.png)
PDF] Fuzzy Extractors: How to Generate Strong Keys from Biometrics and Other Noisy Data | Semantic Scholar

Typical scenario of a Fuzzy Extractor II. PRELIMINARIES AND ASSUMPTIONS | Download Scientific Diagram

A secure fuzzy extractor based biometric key authentication scheme for body sensor network in Internet of Medical Things - ScienceDirect

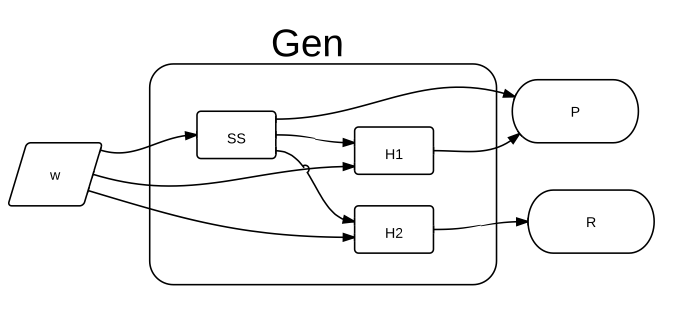
Fuzzy Extractor. Gen generates public data P and a near-uniform key S .... | Download Scientific Diagram

Secure Sketch and Fuzzy Extractor with Imperfect Randomness: An Information-Theoretic Study | SpringerLink
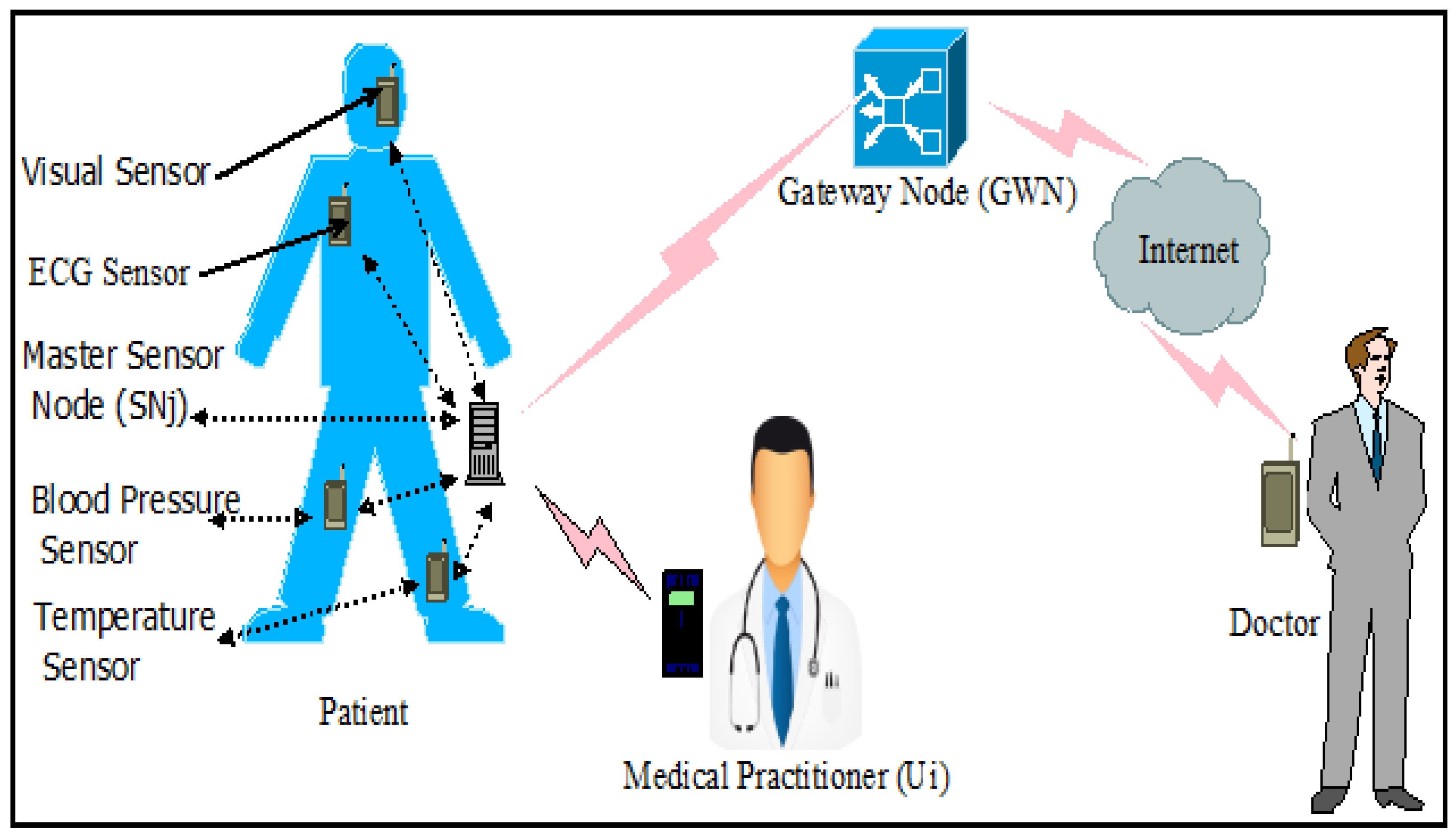
Information | Free Full-Text | Fuzzy Extractor and Elliptic Curve Based Efficient User Authentication Protocol for Wireless Sensor Networks and Internet of Things
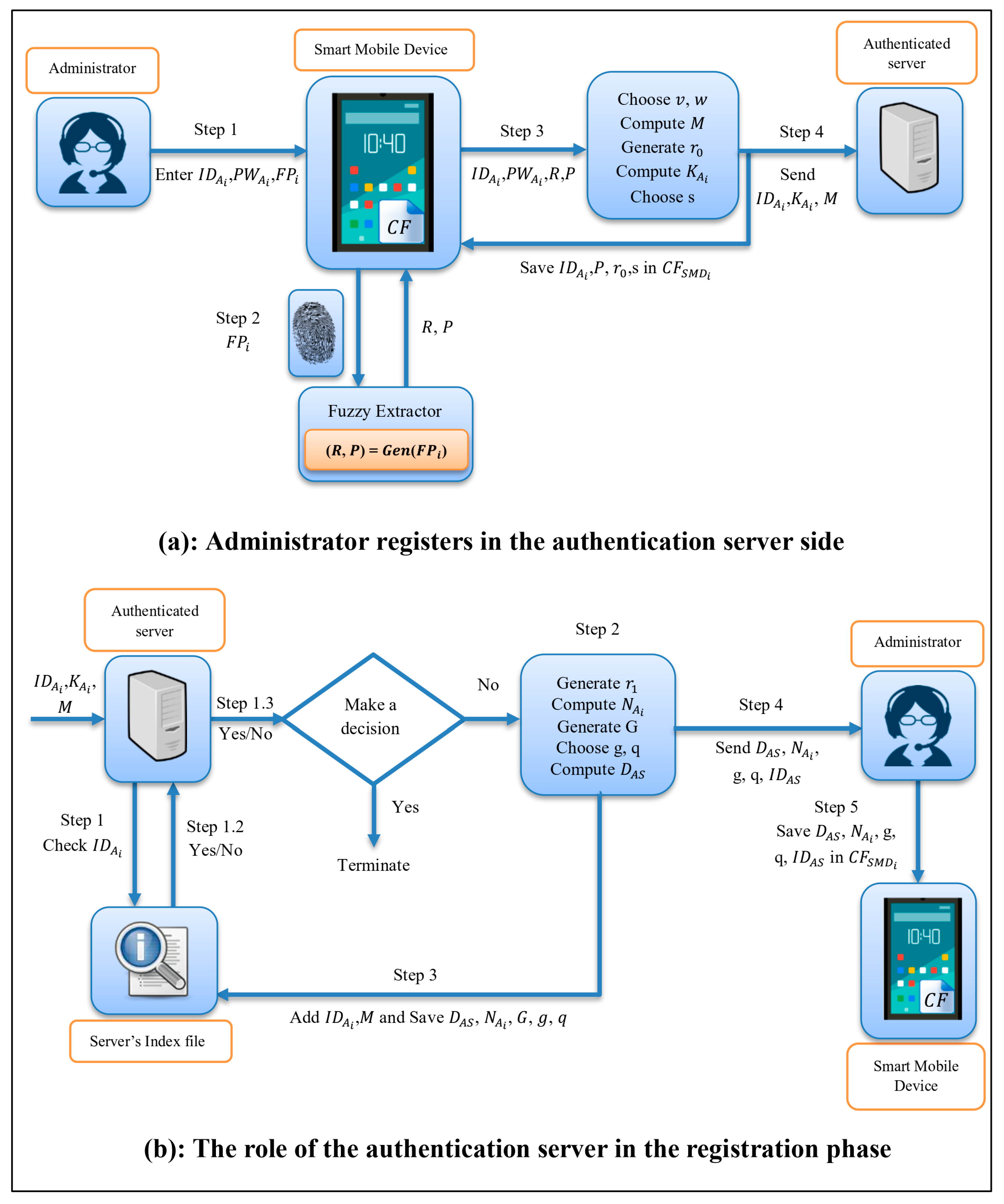
Cryptography | Free Full-Text | Efficient and Flexible Multi-Factor Authentication Protocol Based on Fuzzy Extractor of Administrator's Fingerprint and Smart Mobile Device
A system for a fuzzy extractor To generate the key in fuzzy extractor... | Download Scientific Diagram

Lossless fuzzy extractor enabled secure authentication using low entropy noisy sources - ScienceDirect
![PDF] The Implementation of Fuzzy Extractor is Not Hard to Do : An Approach Using PUF Data | Semantic Scholar PDF] The Implementation of Fuzzy Extractor is Not Hard to Do : An Approach Using PUF Data | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/ac2f335ab9f152d277a7bc72146935532f2794fb/2-Figure2-1.png)





![7C] Neural Fuzzy Extractors - YouTube 7C] Neural Fuzzy Extractors - YouTube](https://i.ytimg.com/vi/Y-sSh3-HDr8/maxresdefault.jpg)