Prevention Across the Cyber Attack Lifecycle with Palo Alto Networks - Exclusive Networks - Switzerland FR
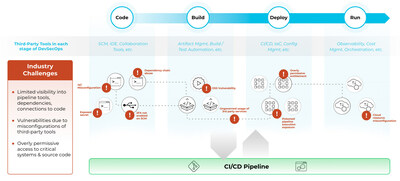
Palo Alto Networks Introduces CI/CD Security, Becoming the First CNAPP to Extend Security into the Software Delivery Pipeline
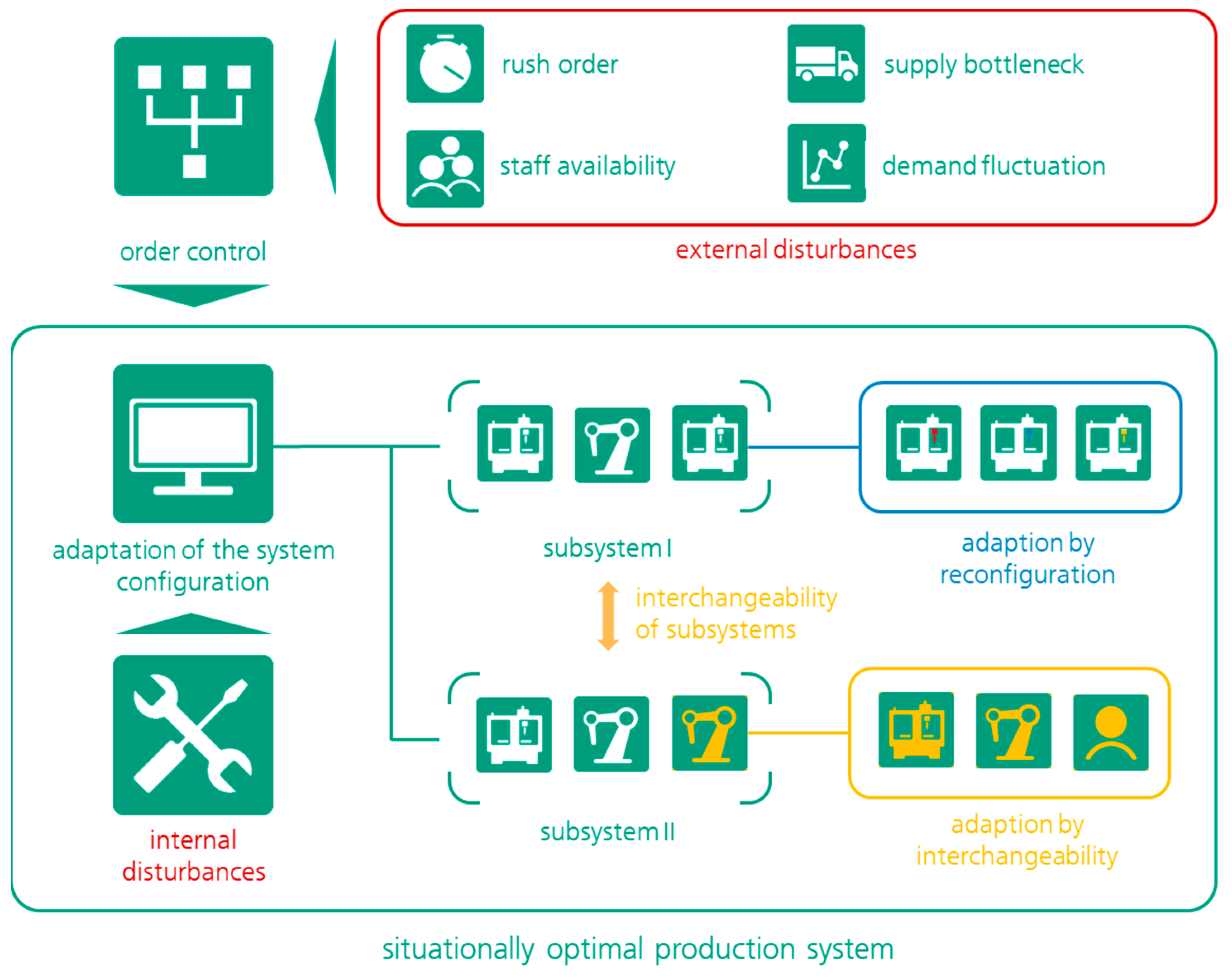
Applied Sciences | Free Full-Text | Increasing Resilience of Production Systems by Integrated Design

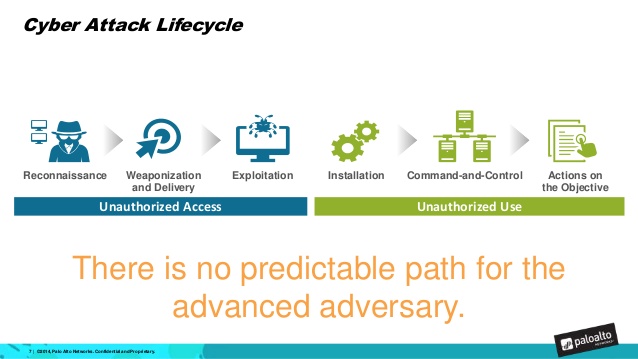
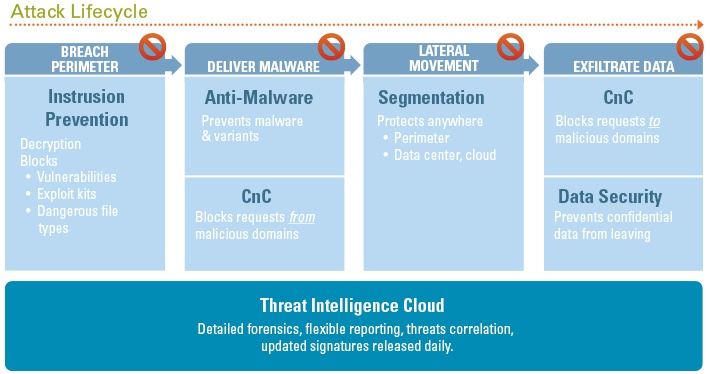
Given the Cyber-Attack Lifecycle diagram, identify the stage in which the attacker can run malicious code against a targeted machine.
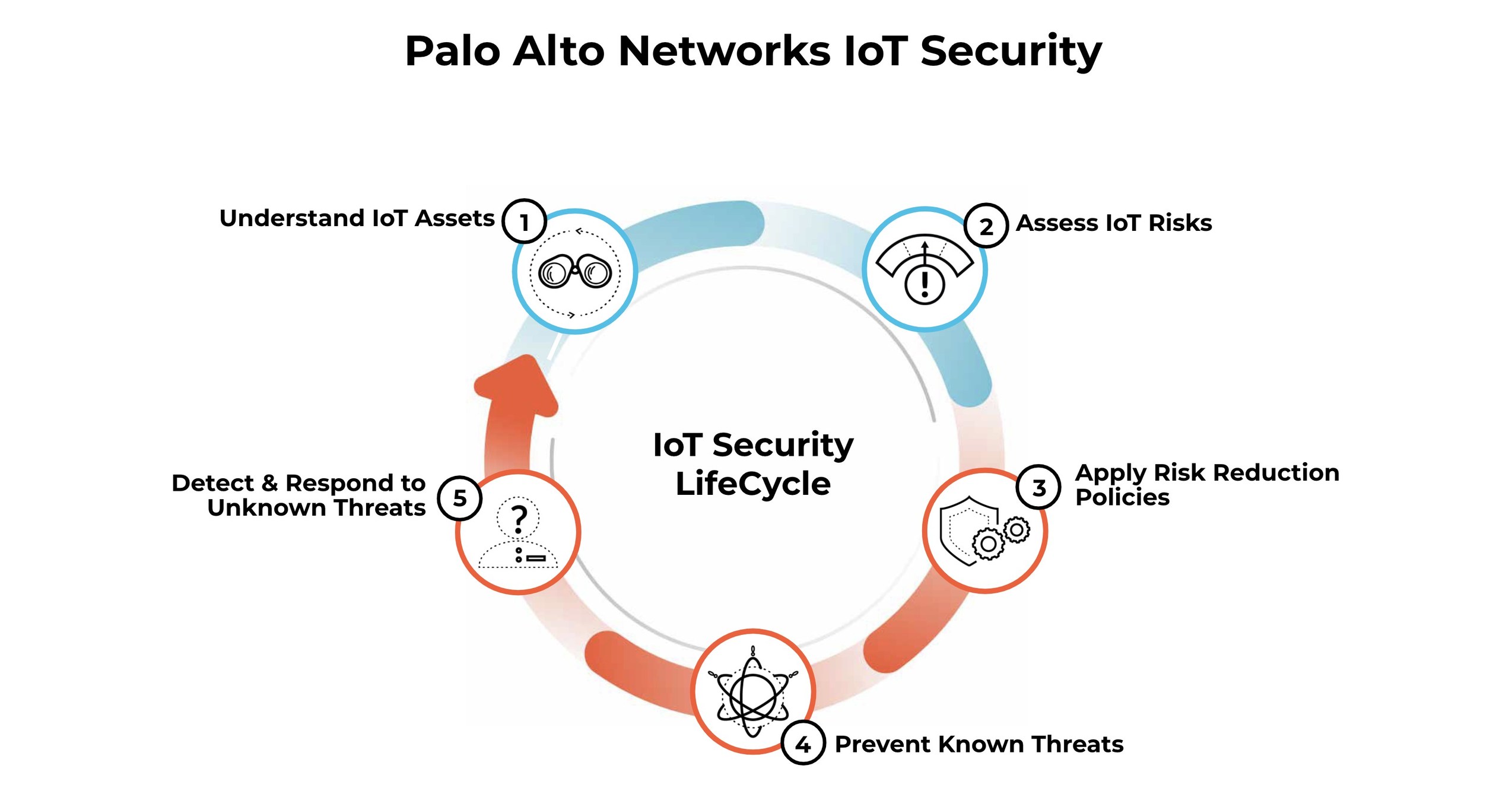
Palo Alto Networks Expands IoT Security to Healthcare -- Dramatically Simplifying the Challenges of Securing Medical Devices
Palo Alto Networks Certified Network Security Administrator (PCNSA) Exam Questions and Answers - Page 2 of 10