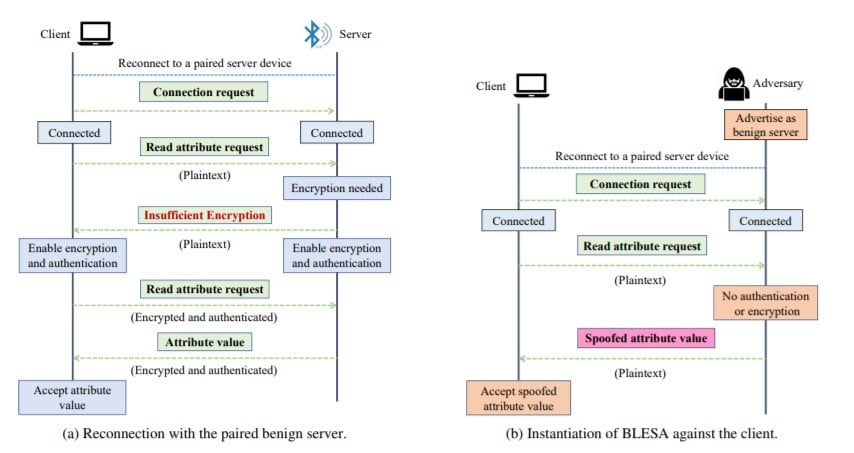
Bluetooth Reconnection Flaw Could Lead to Spoofing Attacks - Department of Computer Science - Purdue University
Security and Privacy Threats for Bluetooth Low Energy in IoT and Wearable Devices: A Comprehensive Survey

BIAS, una nueva vulnerabilidad en Bluetooth que afecta a todos los dispositivos no actualizados recientemente

The Hacker News - Spooftooph 0.5.2 - Automated spoofing or cloning Bluetooth device. Cloning this information effectively allows Bluetooth device to hide in plain site. Get here - http://toolsyard.thehackernews.com/2012/11/spooftooph-052-automated ...



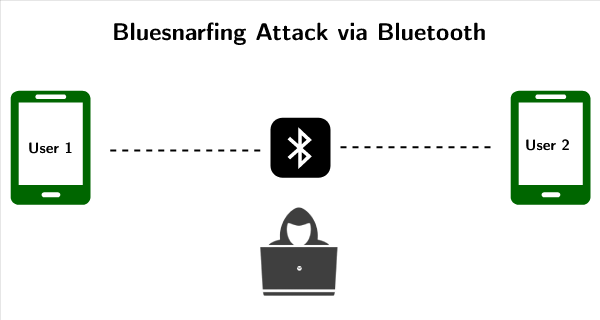
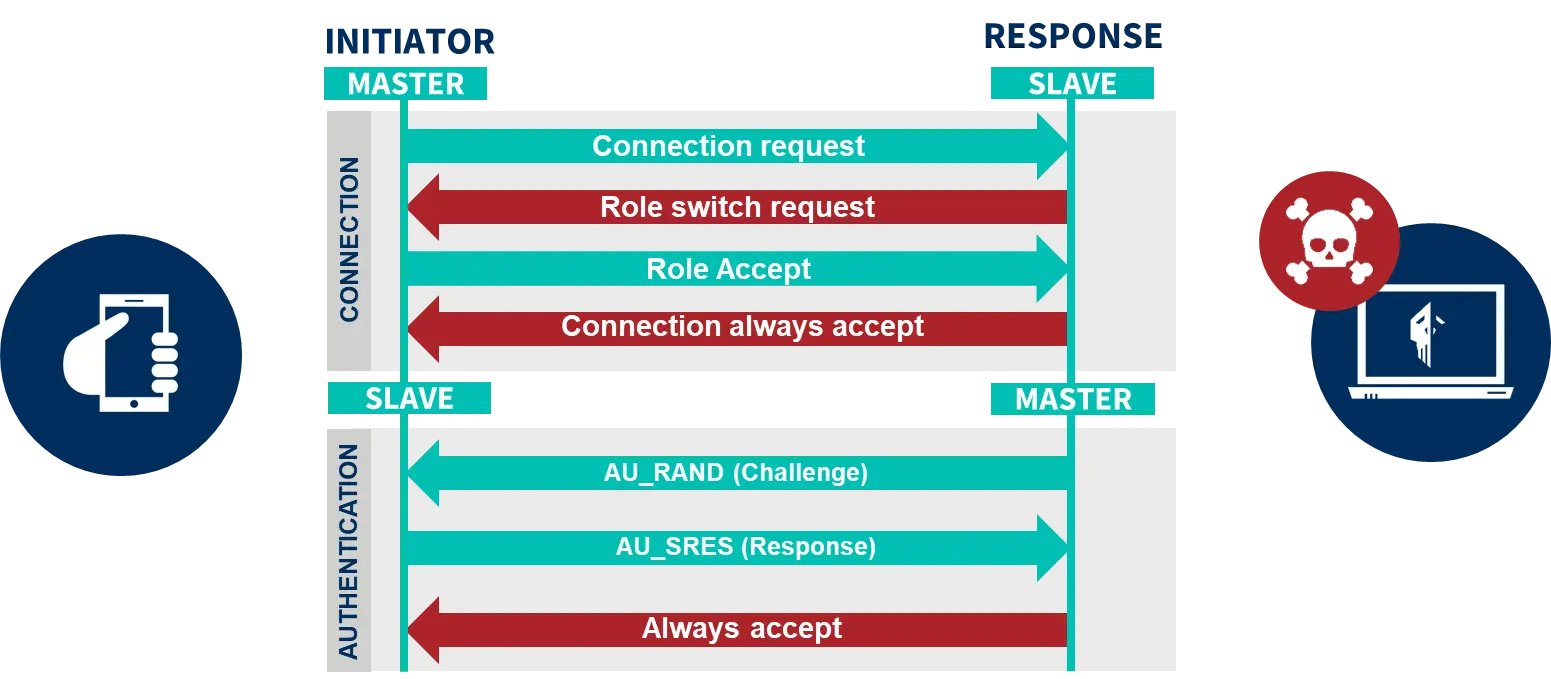





![PDF] BlueShield: Detecting Spoofing Attacks in Bluetooth Low Energy Networks | Semantic Scholar PDF] BlueShield: Detecting Spoofing Attacks in Bluetooth Low Energy Networks | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/e715459789959d45ba354e93f7413d48645267e4/3-Figure2-1.png)