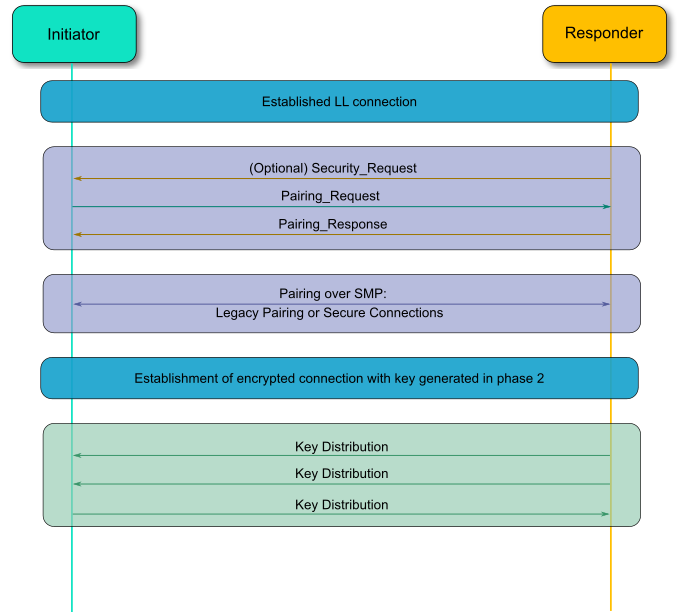
A Basic Introduction to BLE 4.x Security - RF and Wireless - Electronic Component and Engineering Solution Forum - TechForum │ Digi-Key
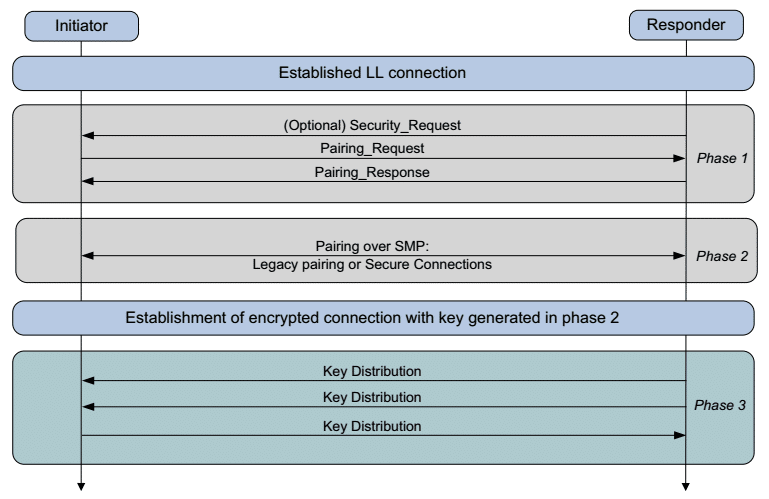
How to Implement Bluetooth Low Energy Security and Privacy in Wireless Devices - Contract Engineering, Product Design & Development Company - Cardinal Peak

Figure 1 from On the (In)security of Bluetooth Low Energy One-Way Secure Connections Only Mode | Semantic Scholar
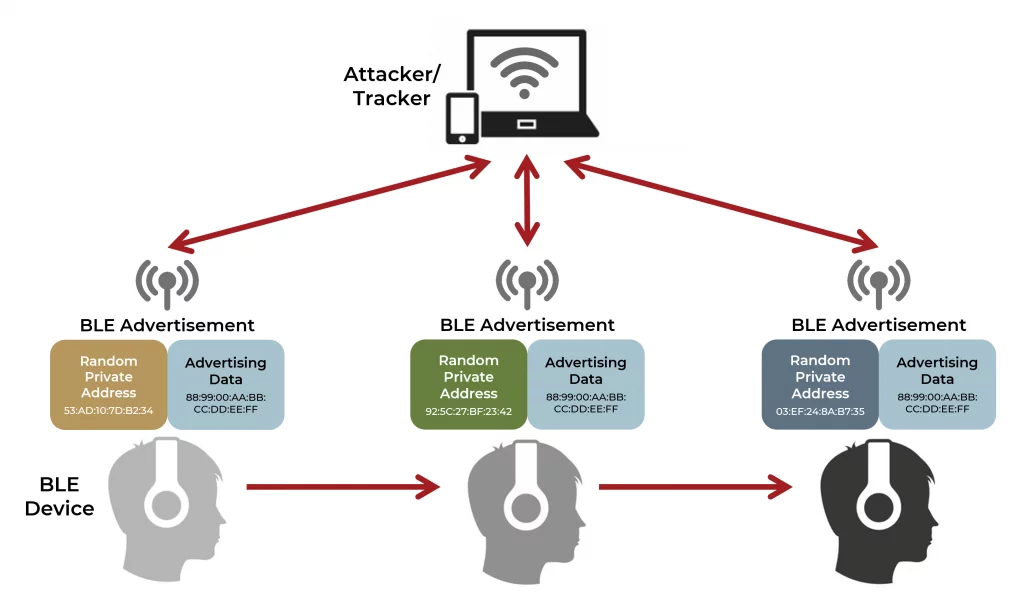
How to Implement Bluetooth Low Energy Security and Privacy in Wireless Devices - Contract Engineering, Product Design & Development Company - Cardinal Peak
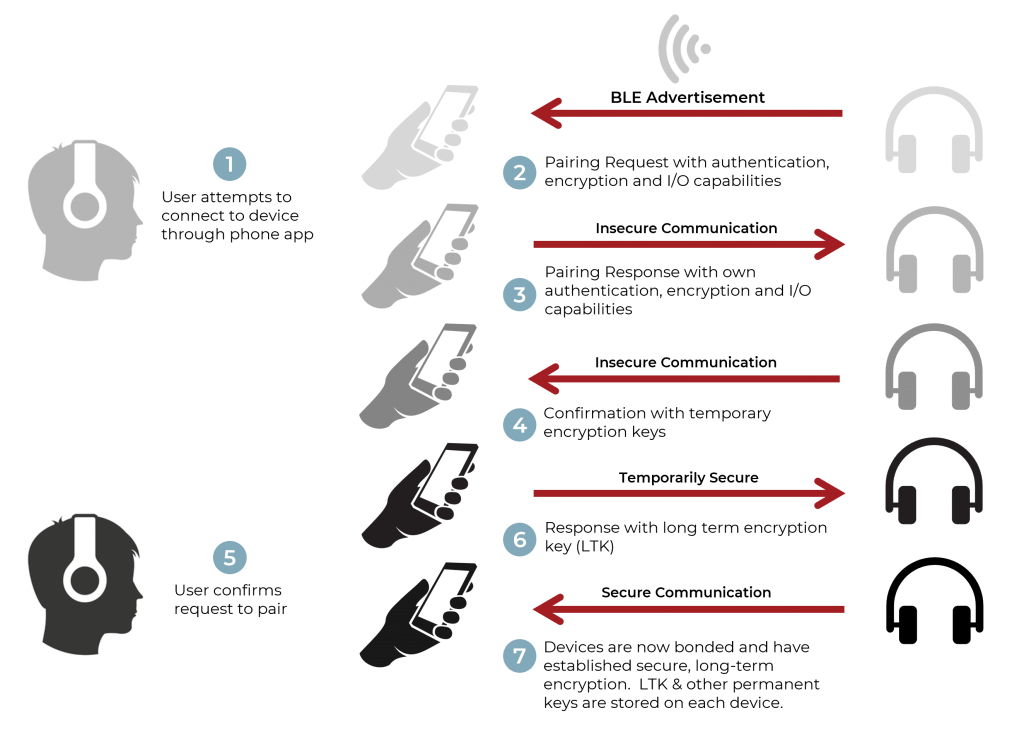
How to Implement Bluetooth Low Energy Security and Privacy in Wireless Devices - Contract Engineering, Product Design & Development Company - Cardinal Peak

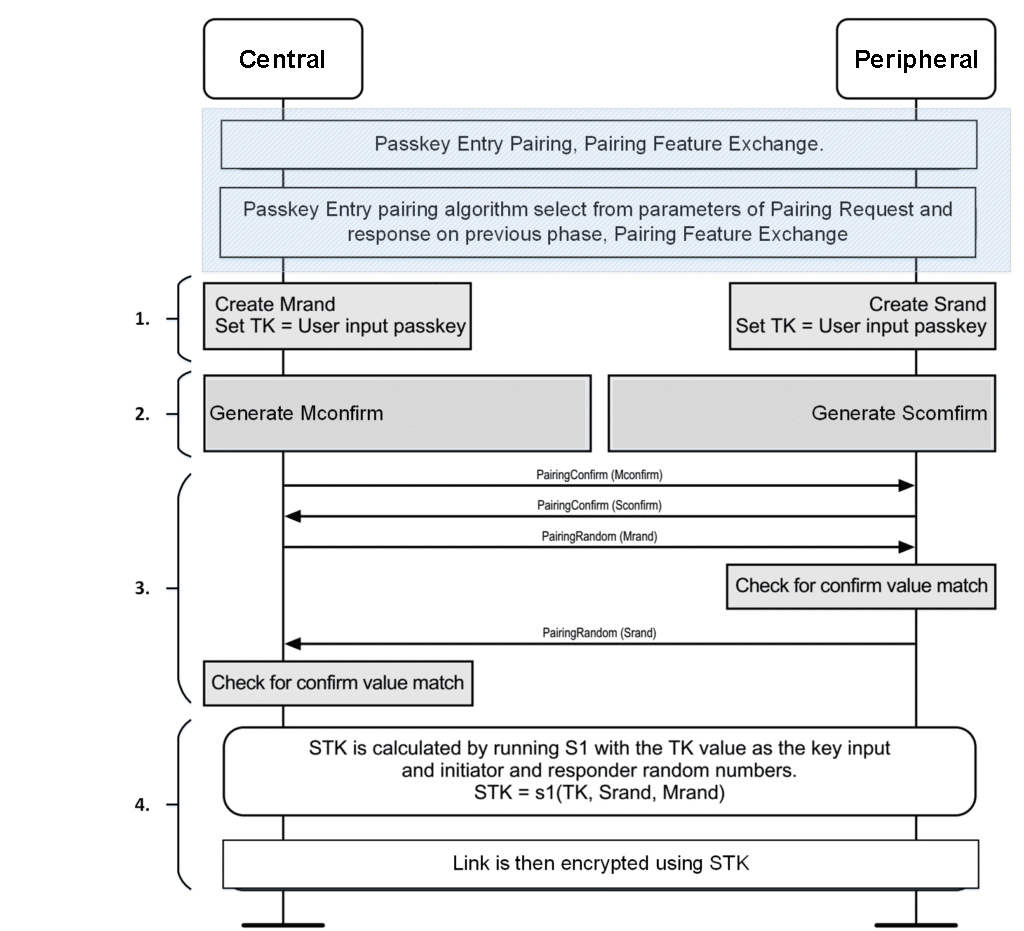
Figure 1 from Pairing and Authentication Security Technologies in Low-Power Bluetooth | Semantic Scholar
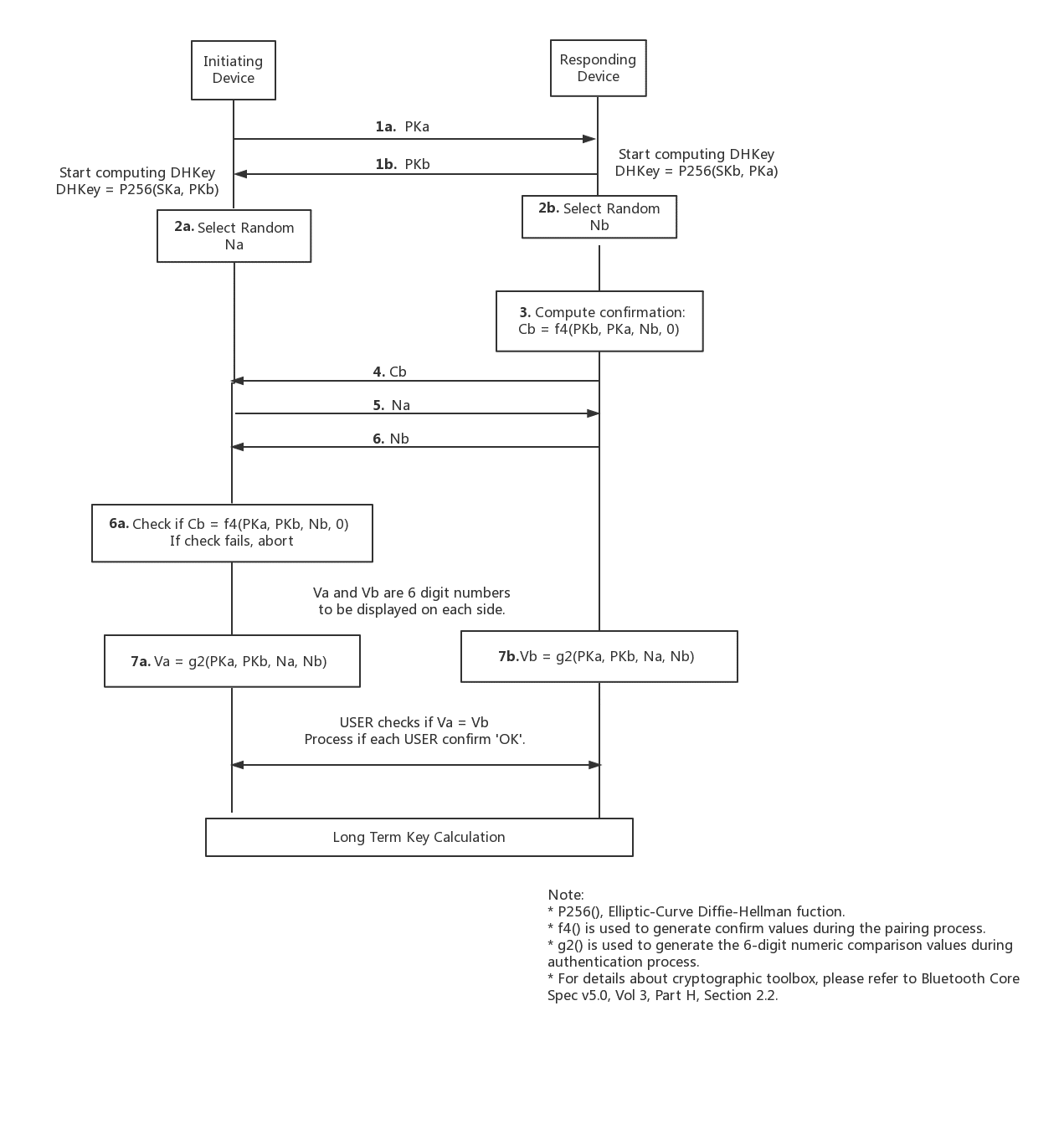
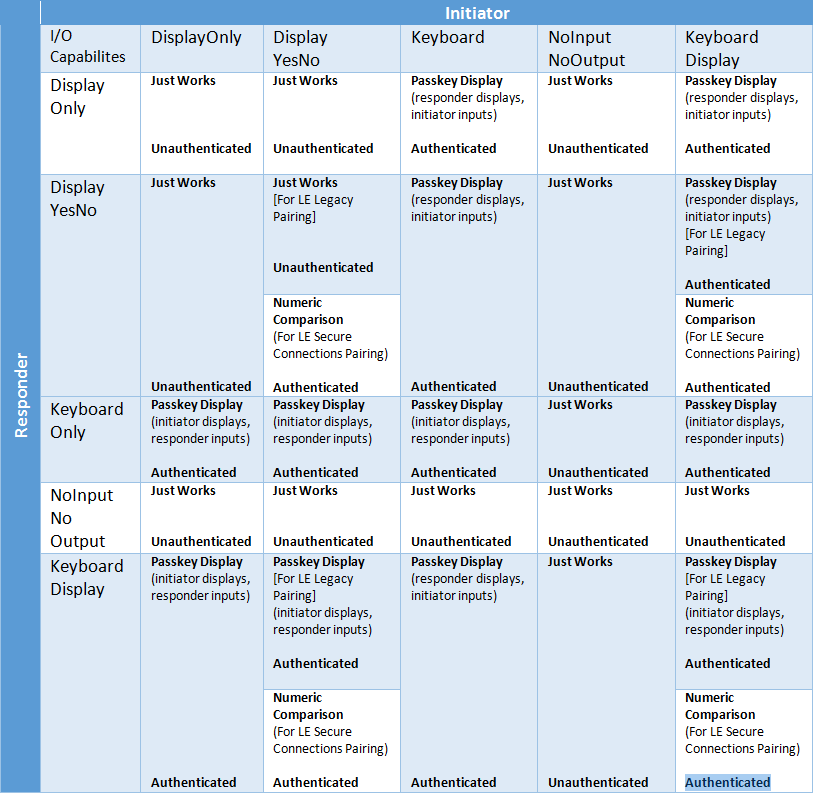
Bluetooth Pairing Part 4:Bluetooth Low EnergySecure Connections -Numeric Comparison | Bluetooth® Technology Website
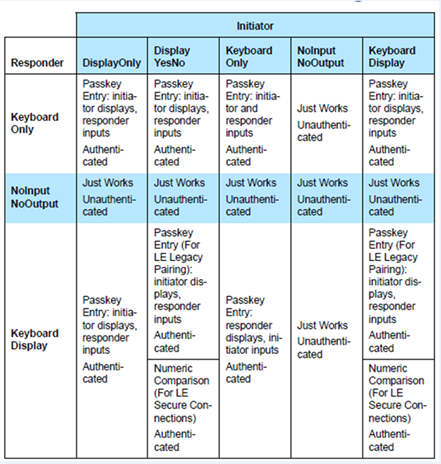
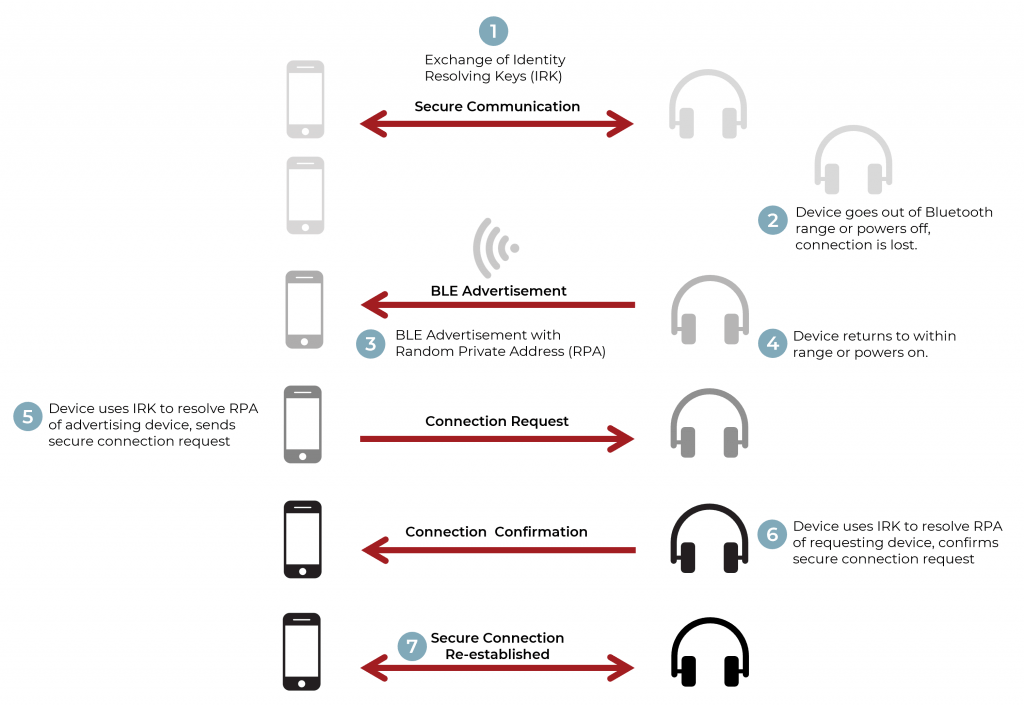
Make your Bluetooth Low Energy IoT device more secure with Visible Light Communication - Blogs - Nordic Blog - Nordic DevZone