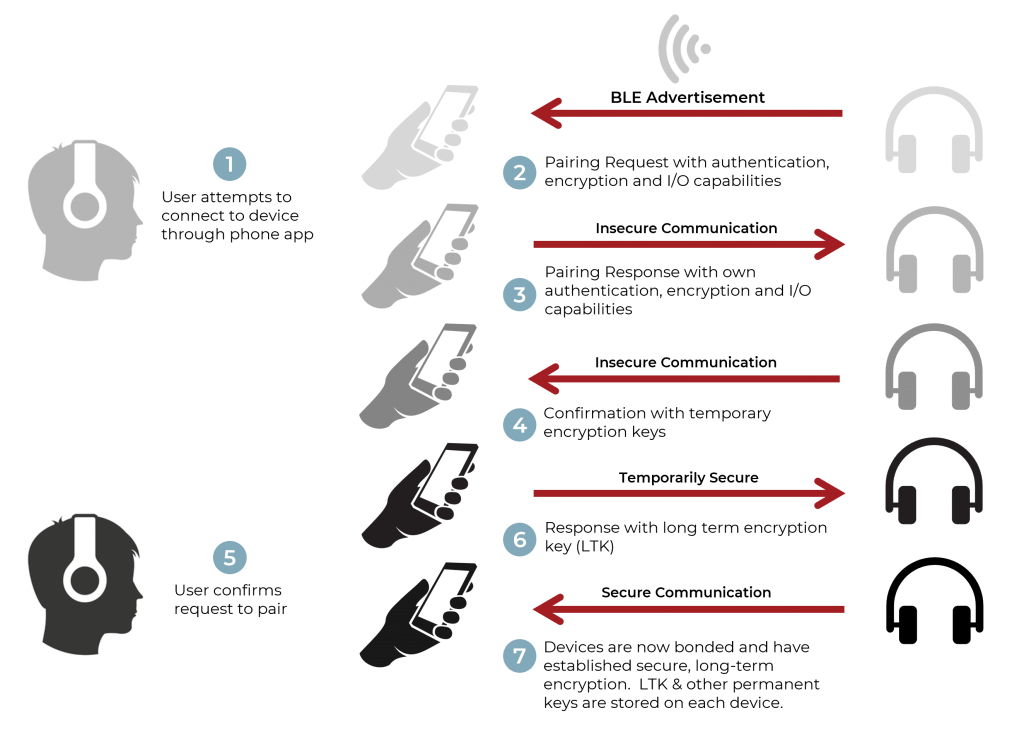
![PDF] On the (In)security of Bluetooth Low Energy One-Way Secure Connections Only Mode | Semantic Scholar PDF] On the (In)security of Bluetooth Low Energy One-Way Secure Connections Only Mode | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/f19272435837aa6e51eebb874016ef152c7d32d3/3-Figure1-1.png)
PDF] On the (In)security of Bluetooth Low Energy One-Way Secure Connections Only Mode | Semantic Scholar
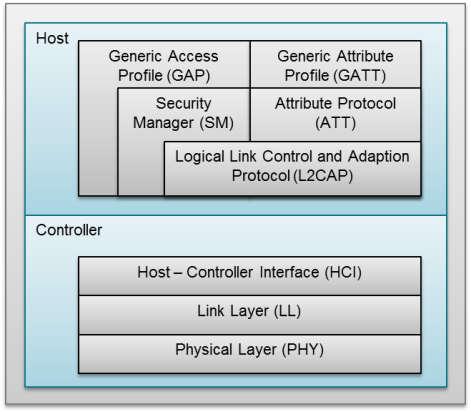
Bluetooth Low Energy Protocol Stack — Bluetooth Low Energy Software Developer's Guide 3.00.00 documentation
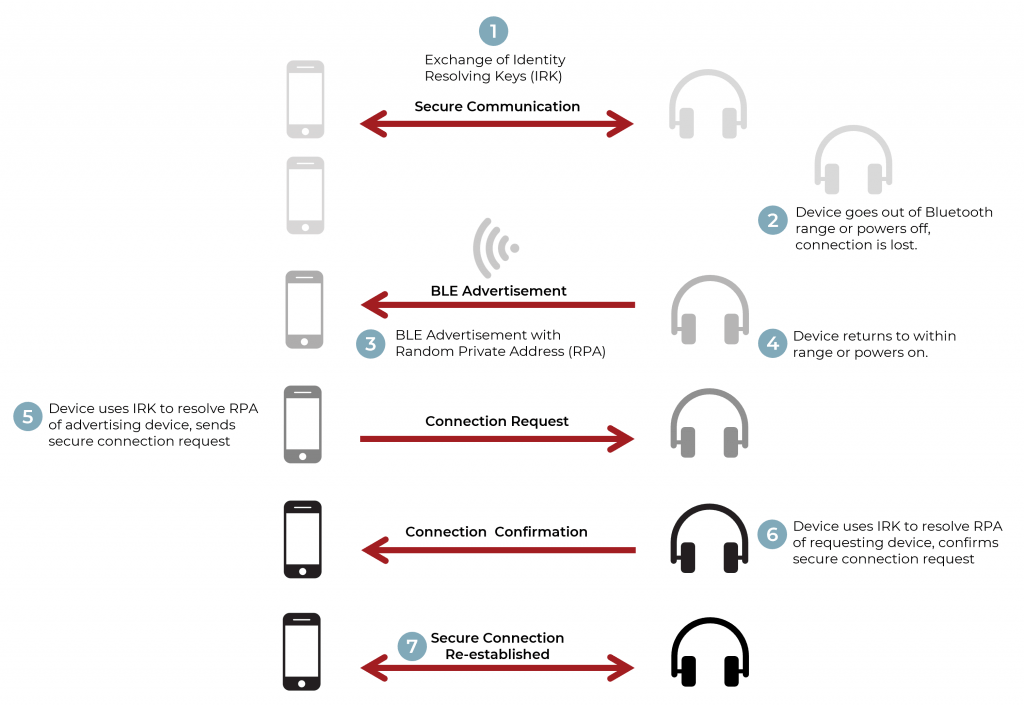
How to Implement Bluetooth Low Energy Security and Privacy in Wireless Devices - Contract Engineering, Product Design & Development Company - Cardinal Peak

A Basic Introduction to BLE 4.x Security - RF and Wireless - Electronic Component and Engineering Solution Forum - TechForum │ Digi-Key
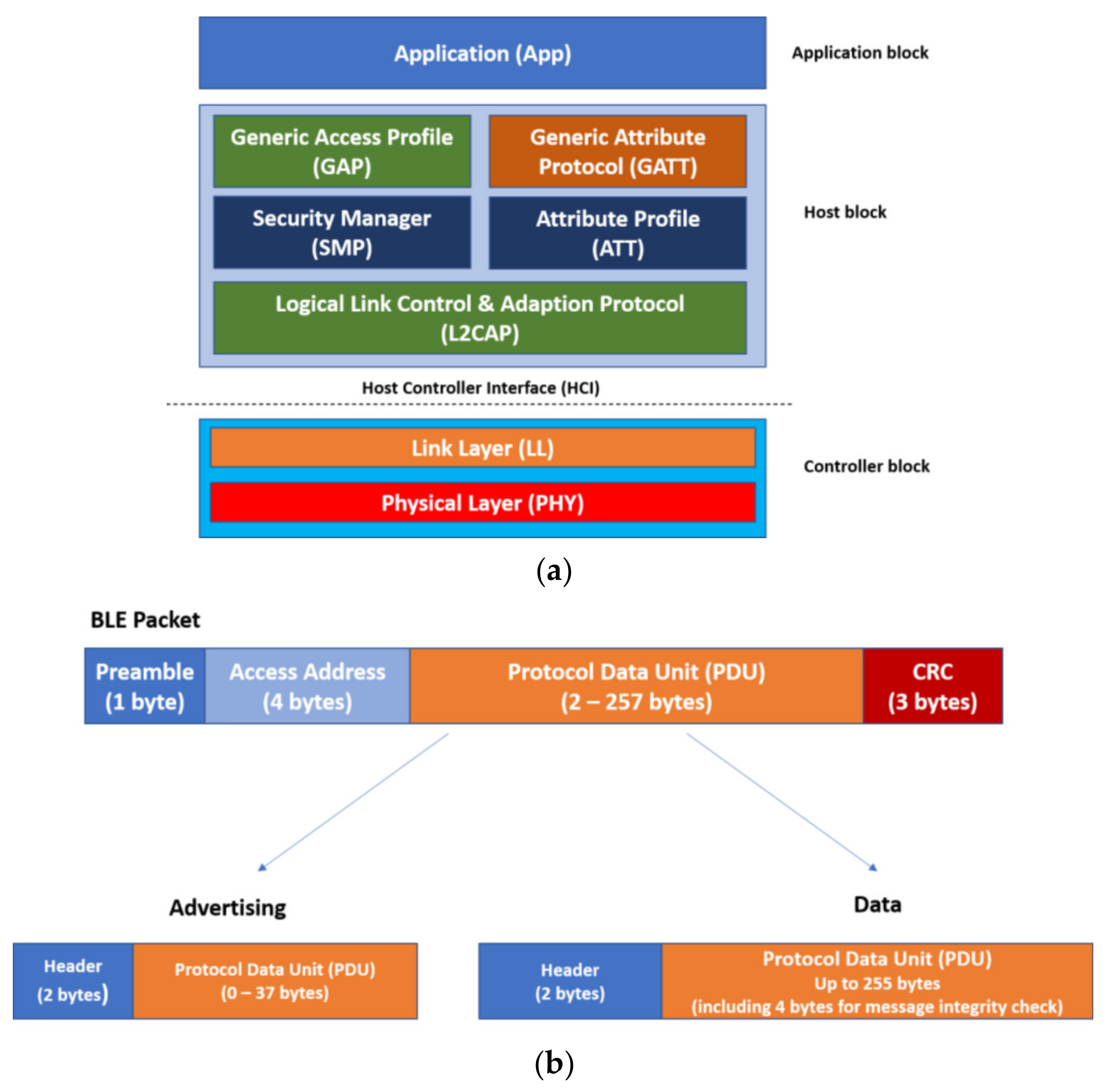
Sensors | Free Full-Text | On the Security of Bluetooth Low Energy in Two Consumer Wearable Heart Rate Monitors/Sensing Devices

Develop your own Bluetooth Low Energy Applications: for Raspberry Pi, ESP32 and nRF52 with Python, Arduino and Zephyr : Vervloesem, Koen: Amazon.es: Libros

A Basic Introduction to BLE 4.x Security - RF and Wireless - Electronic Component and Engineering Solution Forum - TechForum │ Digi-Key
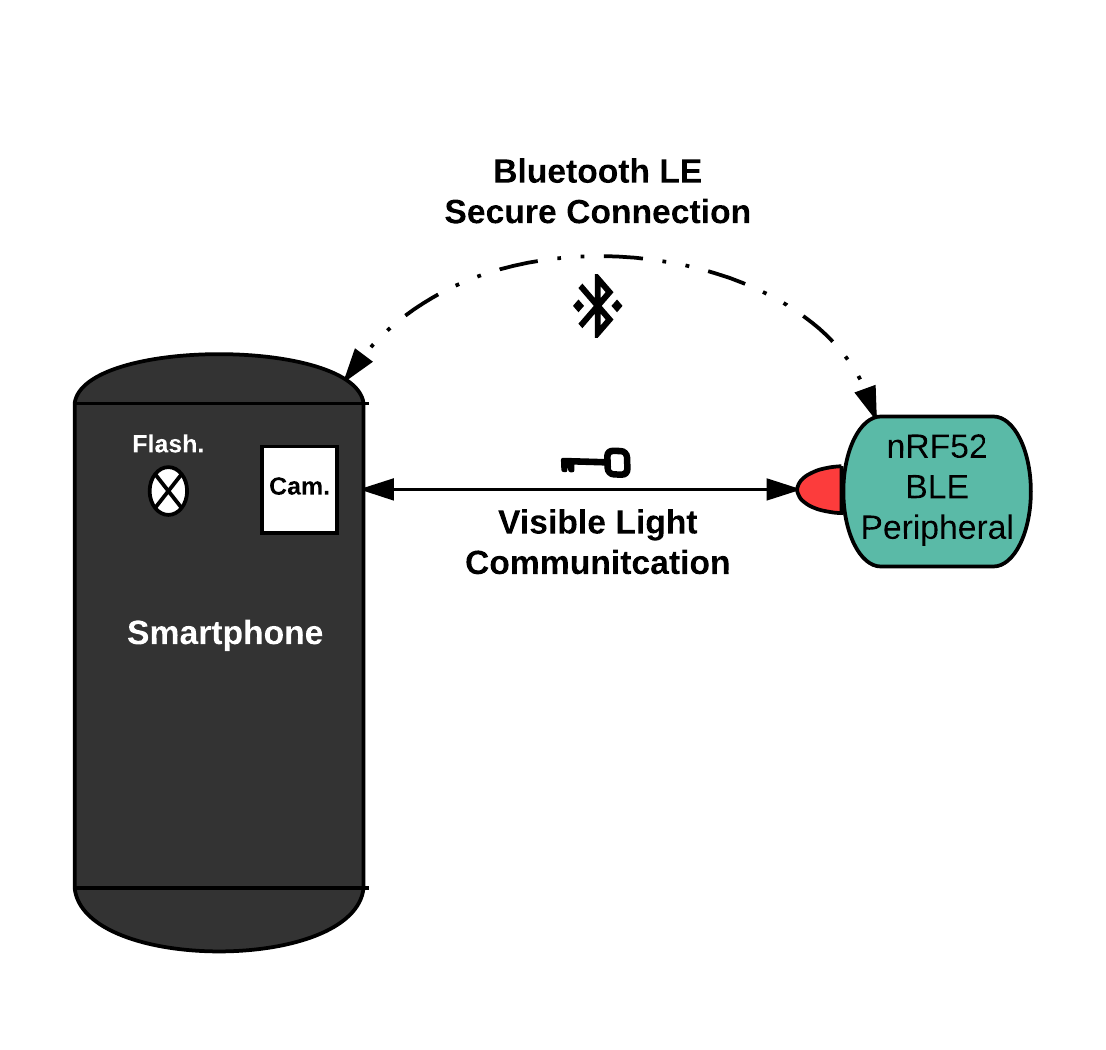
Make your Bluetooth Low Energy IoT device more secure with Visible Light Communication | by Alexis Duque | Rtone IoT Security | Medium