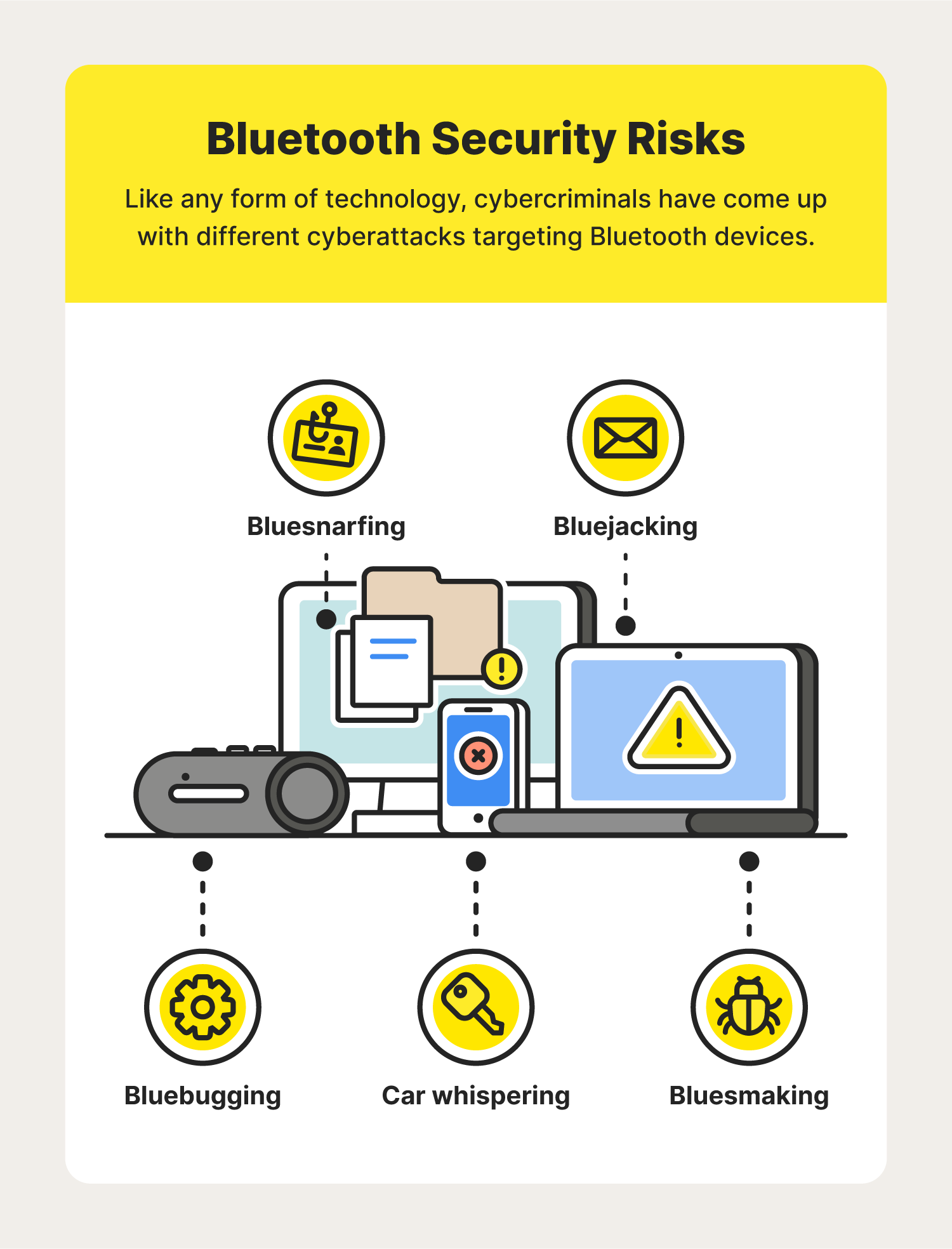
A Basic Introduction to BLE 4.x Security - RF and Wireless - Electronic Component and Engineering Solution Forum - TechForum │ Digi-Key

Guide to improve the security posture of Bluetooth Low Energy-enabled applications | by Kang Hao | CSG @ GovTech | Medium
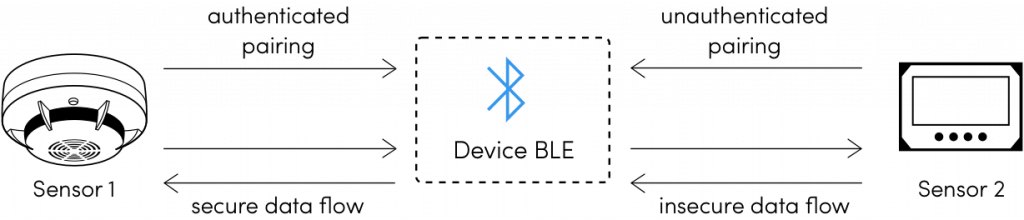
![PDF] On the (In)security of Bluetooth Low Energy One-Way Secure Connections Only Mode | Semantic Scholar PDF] On the (In)security of Bluetooth Low Energy One-Way Secure Connections Only Mode | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/f19272435837aa6e51eebb874016ef152c7d32d3/3-Figure1-1.png)
PDF] On the (In)security of Bluetooth Low Energy One-Way Secure Connections Only Mode | Semantic Scholar