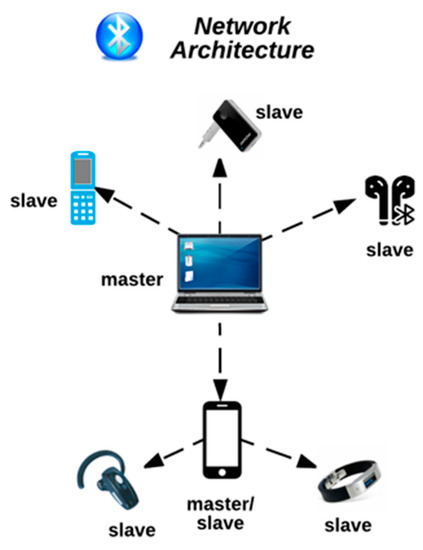
Detector anti espía Detector anti-eAvesdropping Teléfono móvil Cámara anti-Sneak Equipo anti-monitoreo Detector de posicionamiento de GPS inalámbrico por GPS Buscador de cámara de dispositivo de escuc : Amazon.es: Electrónica

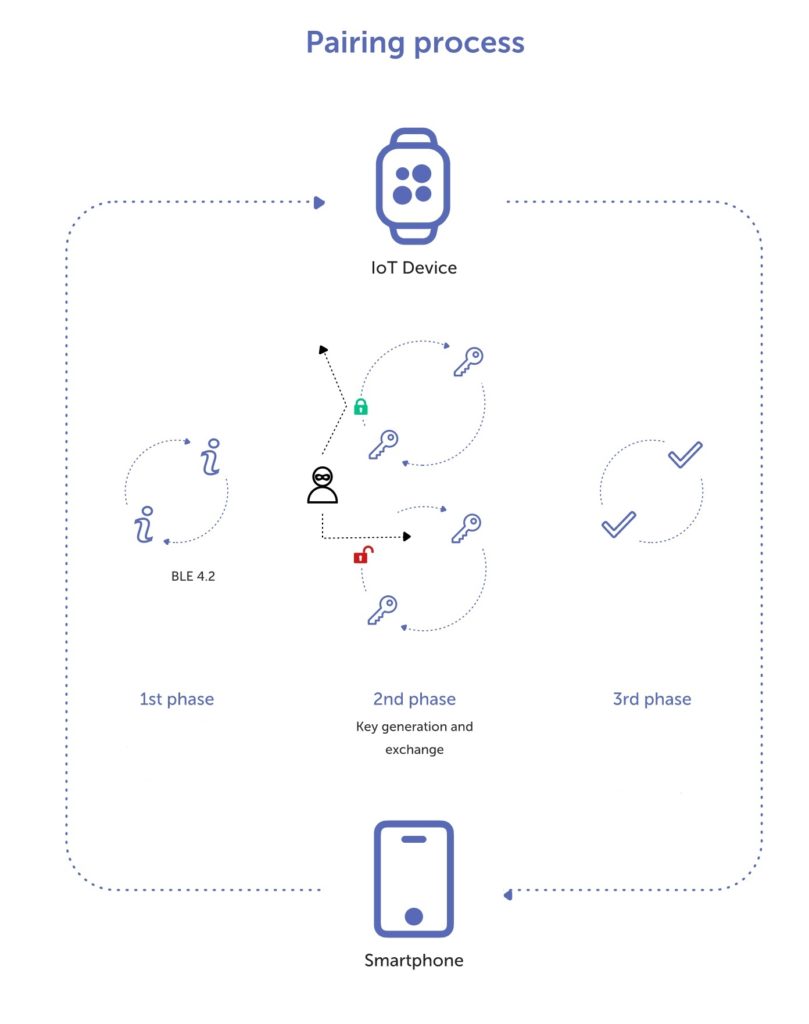
Sensors | Free Full-Text | Eavesdropping Vulnerability and Countermeasure in Infrared Communication for IoT Devices

Suministro Al Por Mayor Hope M60 Bluetooth Mini Dialer Teléfonos Móviles Auricular Inalámbrico Bluetooth Dual SIM 550 Mah Batería Tiempo De Espera Prolongado Para Diseño De Deportes Al Aire Libre De Mixpackage,

Anti Sound Recording Bug Audio Eavesdropping 37 Emission Hole Of Ultrasound Interference Anti Wiret | Fruugo ES