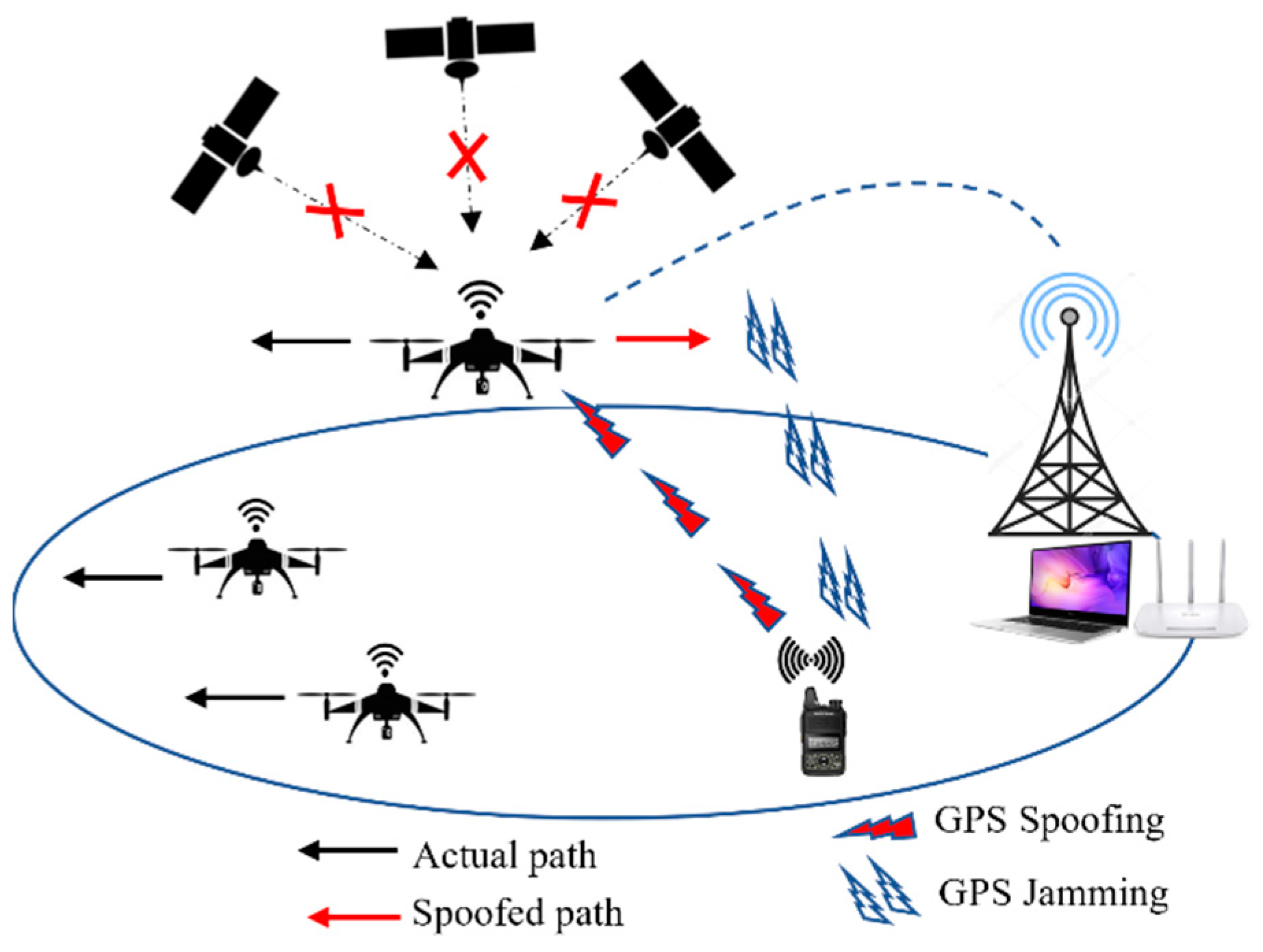
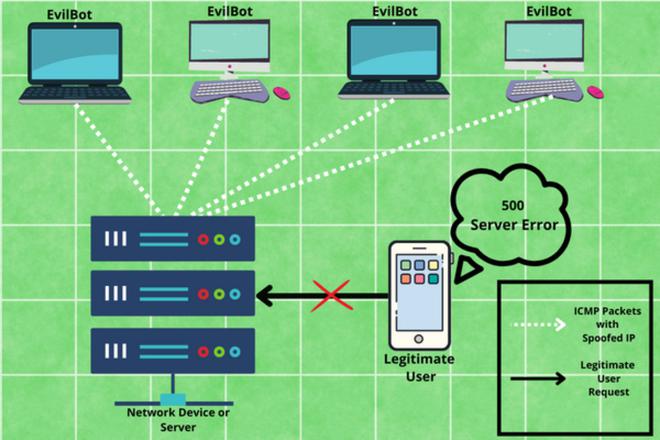
JSAN | Free Full-Text | DDoS Attack and Detection Methods in Internet-Enabled Networks: Concept, Research Perspectives, and Challenges

Bluesmack | Corrupting my own Bluetooth Device | Denial of Service(DOS) Attack | 2021 | Devil Emox - YouTube

JSAN | Free Full-Text | DDoS Attack and Detection Methods in Internet-Enabled Networks: Concept, Research Perspectives, and Challenges



![Identify & Target Bluetooth Devices with Bettercap [Tutorial] - YouTube Identify & Target Bluetooth Devices with Bettercap [Tutorial] - YouTube](https://i.ytimg.com/vi/YDpjGTojByw/maxresdefault.jpg)